Incident Details
| Victimized Company: | Football Australia |
| Incident Dates: | 2022-03-26 (approx) to 2024-02-01 |
| Disclosure Date: | 2024-02-01 |
| Current Status: | N/A |
| Victimized Company: | Football Australia |
| Incident Dates: | 2022-03-26 (approx) to 2024-02-01 |
| Disclosure Date: | 2024-02-01 |
| Current Status: | N/A |
Football Australia, the national governing authority for the sport, embedded an AWS Access Key in their website that granted access to 126 S3 Buckets containing sensitive information for players and fans.
An AWS long-term Access Key was embedded into the source code for the Football Australia website. As seen in the screenshot below (courtesy CyberNews) it looks related to Cognito:
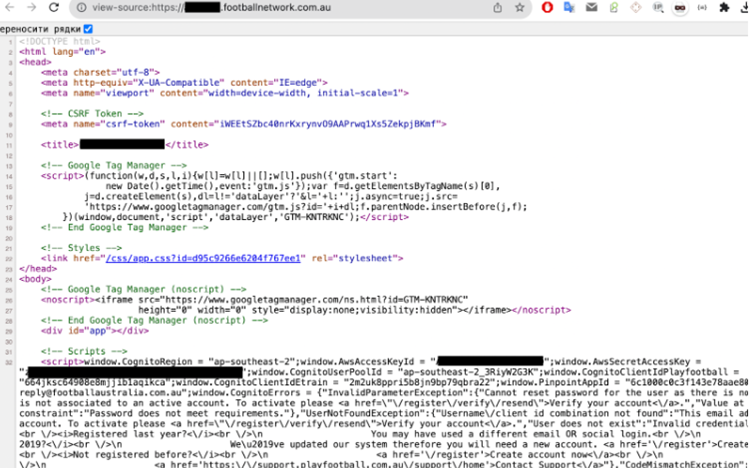
Moreover, one of the buckets was left completely unprotected, which means it was left public and accessible without any keys. The public digital storage container contained football players’ passports and contracts.
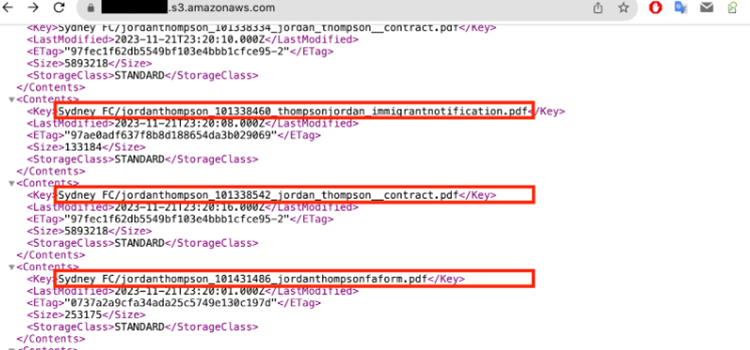 Image by Cybernews.
Image by Cybernews.
Per a statement from Football Australia to CyberNews:
the exposed data includes:
- Personal identifiable information of players
- Ticket purchase information
- Internal infrastructure details
- Source code of the digital infrastructure
- Scripts of the digital infrastructure
| Date | Event |
|---|---|
| March 2022 | 681 days prior to disclosure, the access keys are exposed (source: Sydney Morning Herald) |
| February 1, 2024 | Responsible Disclosure disclosed |
None yet.